A safety analysis agency says it found an “simply” exploitable vulnerability in a door entry safety system utilized in authorities buildings and house complexes, however warns that the vulnerability can’t be fastened.
Norwegian safety firm Promon says the bug impacts a number of Aiphone GT fashions that use NFC know-how, typically present in contactless bank cards, and permits unhealthy actors to doubtlessly achieve entry to delicate services by brute-forcing the door entry system’s safety code.
Door entry techniques permit safe entry to buildings and residential complexes, however have turn into more and more digitized, making them susceptible to each bodily and distant compromise.
Aiphone counts each the White Home and the U.Ok. Parliament as clients of the affected techniques, in line with firm brochures seen by TechCrunch.
Promon safety researcher Cameron Lowell Palmer stated a would-be intruder can use an NFC-capable cellular gadget to quickly cycle by way of each permutation of a four-digit “admin” code used to safe every Aiphone GT door system. As a result of the system doesn’t restrict what number of instances a code might be tried, Palmer stated it takes solely minutes to cycle by way of every of the ten,000 doable four-digit codes utilized by the door entry system. That code might be punched into the system’s keypad, or transmitted to an NFC tag, permitting unhealthy actors to doubtlessly entry restricted areas with out having to the touch the system in any respect.
In a video shared with TechCrunch, Palmer constructed a proof-of idea Android app that allowed him to test each four-digit code on a susceptible Aiphone door entry system in his check lab. Palmer stated the affected Aiphone fashions don’t retailer logs, permitting a foul actor to bypass the system’s safety with out leaving a digital hint.
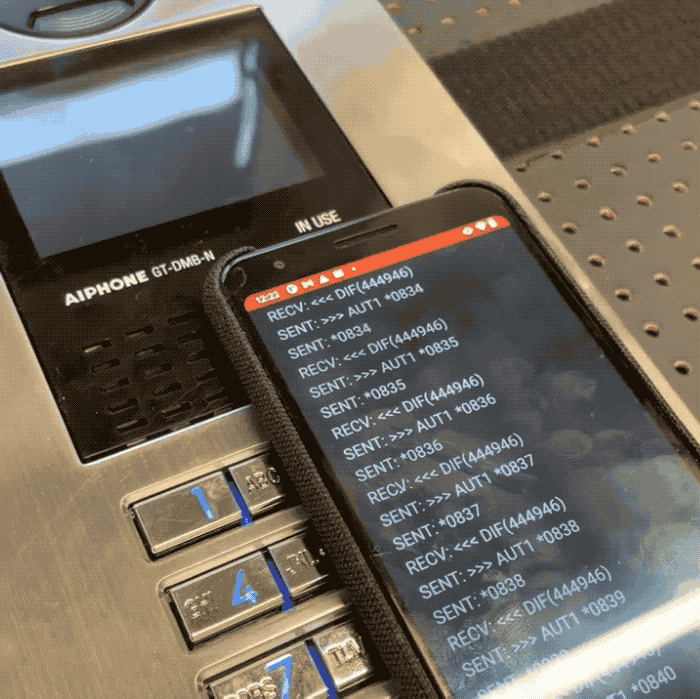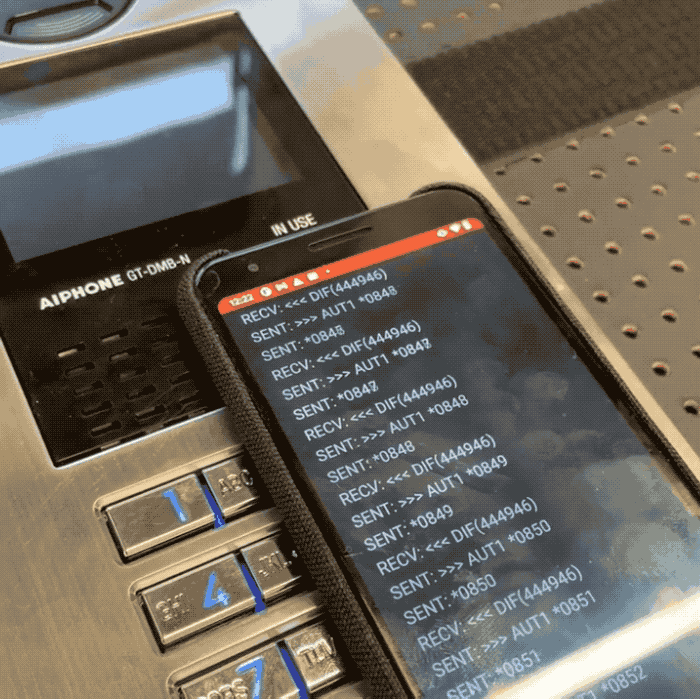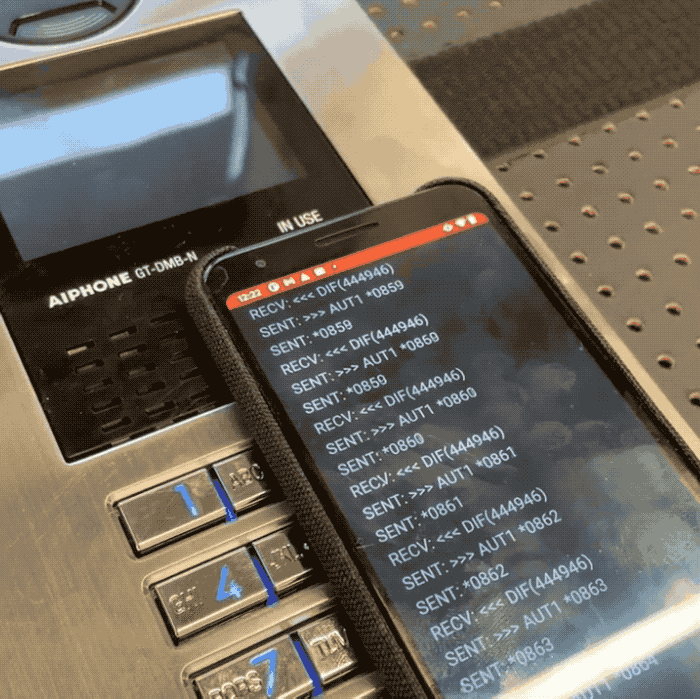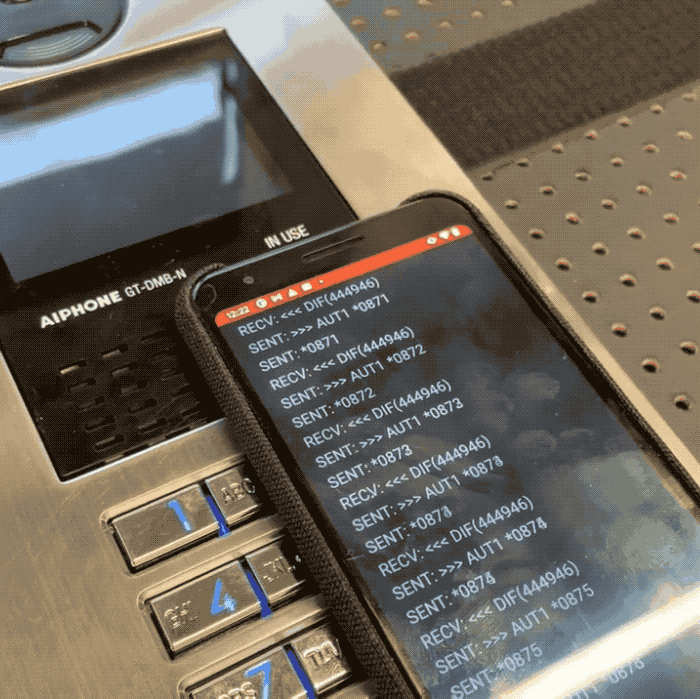
Picture Credit: Cameron Lowell Palmer / Promon
Palmer disclosed the vulnerability to Aiphone in late June 2021. Aiphone informed the safety firm that techniques manufactured earlier than December 7, 2021 are affected and can’t be up to date, however that techniques after this date have a software program repair that limits the speed of door entry makes an attempt.
It’s not the one bug that Promon found within the Aiphone system. Promon additionally stated it found that the app used to arrange the door entry system gives an unencrypted, plaintext file that incorporates the administrator code for the system’s back-end portal. Promon stated that would permit an intruder to additionally entry the knowledge wanted to entry restricted areas.
Aiphone spokesperson Brad Kemcheff didn’t reply to requests for remark despatched previous to publication.
Relatedly, a college pupil and safety researcher earlier this 12 months found a “grasp key” vulnerability in a extensively used door entry system constructed by CBORD, a tech firm that gives entry management and fee techniques to hospitals and college campuses. CBORD fastened the bug after the researcher reported the difficulty to the corporate.

