Decentralized applied sciences and blockchain-based platforms have emerged as fashionable tendencies within the area of expertise. Does blockchain serve a transformative influence solely within the type of cryptocurrencies and NFTs? The working of blockchain has created the foundations of web3, a brand new model of the web. Web3, dApps, and sensible contracts are main the world towards a revolutionary future the place customers would have management over their information and on-line experiences.
On the identical time, safety in web3 has additionally emerged as a formidable subject as customers should encounter various kinds of safety threats in web3. The issue with web3 is that you simply can not depend on the inherent safety ideas of web3. For instance, the transparency of sensible contracts on public blockchains can expose various kinds of vulnerabilities to malicious brokers.
Web3 serves as a decentralized model of the online with a peer-to-peer community, the place customers received’t want intermediaries akin to social media corporations, tech giants, and banks. One of many foremost highlights in a web3 safety information would level on the elementary safety ideas related to web3.
The safety ideas in web3 embrace cryptography, which facilitates encryption and safety for information. Equally, blockchain expertise gives a safe ledger for web3 transactions via immutability. Allow us to study extra about web3 safety and finest practices for safeguarding your digital property.
Significance of Safeguarding Digital Property in Web3
Earlier than in search of insights about finest practices for web3 safety, it’s essential to study concerning the significance of safeguarding your digital property. The standard scope of cybersecurity revolved round securing digital property akin to information and folders that didn’t retailer something of financial worth. If a safety answer can safeguard customers from downloading malicious software program or clicking on suspicious web sites, then it’s thought of a dependable device for cybersecurity.
Nevertheless, web3 has modified the definition of digital property with the arrival of cryptocurrencies and NFTs. Customers can depend on blockchain-based decentralized platforms for proudly owning, storing, and controlling digital property, together with cryptocurrencies and NFTs. In a means, web3 turned the web right into a secure deposit field that enables creation, storage, and change of property with financial worth.
The decentralized model of the web launched new variants of safety dangers. Customers should study web3 safety ideas and finest practices to keep away from their beneficial property from theft. It is very important do not forget that web3 removes intermediaries, and the accountability of safeguarding digital property falls on the customers. Due to this fact, it is very important perceive how web3 safety differs from web2 cybersecurity.
Study the basics, challenges and use circumstances of Web3.0 blockchain from Introduction To Web3 E-Guide
Variations between Web2 and Web3 Safety
While you evaluate web2 with web3 when it comes to safety, you will see that that web2 safety breaches are non permanent, and customers can resolve them simply. Alternatively, web3 safety dangers are prone to have huge penalties for customers. For instance, safety breaches in web2 can result in lack of data, akin to names, bank card numbers, or addresses. Such sorts of assaults can result in publicity to delicate data on the web. Nevertheless, bank card corporations may take responsive motion by freezing the playing cards and issuing new playing cards.
The ramifications of web3 are virtually irreversible owing to the immutable nature of blockchain. Moreover, breaches in web3 platforms may imply that hundreds of customers may lose their digital property completely. Web3 safety breaches may additionally harm the repute of web3 platforms, which may final for an prolonged interval.
The web3 cybersecurity infrastructure has a protracted approach to go, as many of the web3 options depend on single-layer safety options. As a matter of truth, the full losses from web3 safety breaches within the first half of 2023 amounted to $655.61 million. Round 108 assaults have led to losses of virtually $471 million. In 2022, the losses attributable to web3 safety breaches amounted to virtually $3.6 billion.
Definition of Web3 Safety
The issues with web3 safety and the large scale of losses attributable to web3 safety breaches have created curiosity about particular measures for safeguarding your digital property. The solutions to ‘What’s web3 safety?’ level to the completely different processes, methods, and methodologies carried out for safeguarding decentralized applied sciences. Web3 safety envisions safety of blockchain-based platforms, decentralized apps, and the digital property of web3 customers.
The distributed mannequin utilized in web3 gives freedom from intermediaries, which improves privateness and transparency. Nevertheless, the transparency exposes web3 to various kinds of threats. As the recognition of DeFi and NFTs continues rising, it is very important search for robust safety measures to safeguard web3 options. You possibly can safeguard your digital property in web3 with a transparent understanding of safety and privateness dangers.
Wish to discover an in-depth understanding of safety threats in DeFi tasks? Enroll now in DeFi Safety Fundamentals Course
What are the Notable Safety and Privateness Threats in Web3?
The best strategy to staying secure towards an issue is to grasp the issue and the related dangers. With a complete understanding of web3 safety dangers, you could find the perfect practices for resolving the threats. The dangers for web3 customers will be categorised into safety and privateness dangers. Allow us to study extra concerning the widespread safety and privateness dangers you could find in web3.
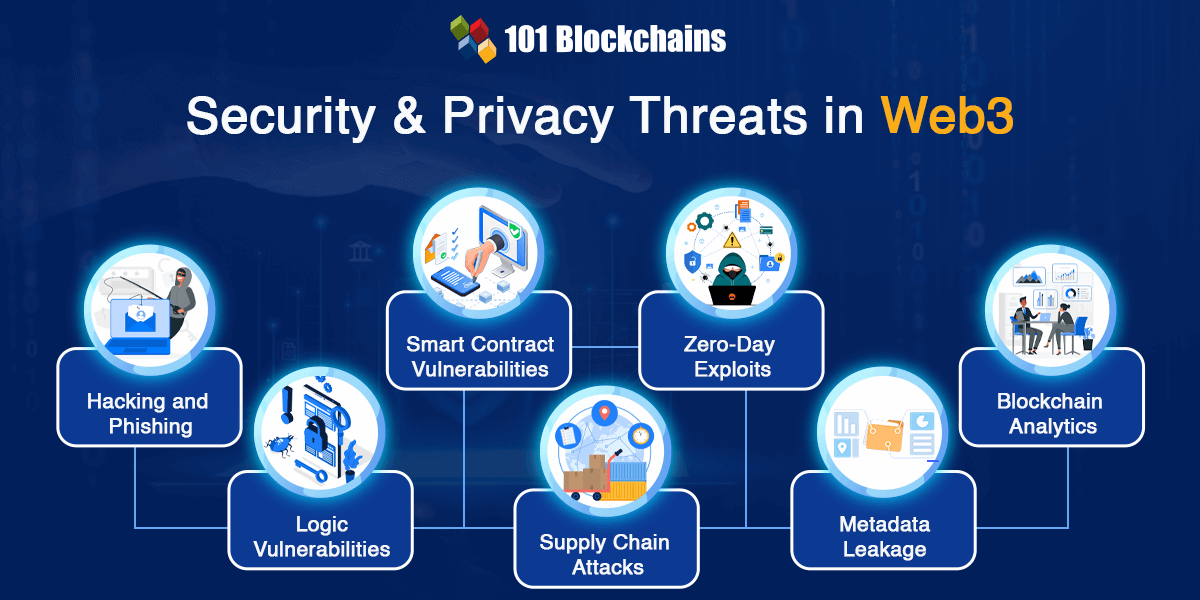
The 2 fashionable web2 assaults which discover their means into discussions about web3 safety embrace hacking and phishing. Any web3 safety information could be incomplete with out mentioning hacking and phishing assaults. Hackers may exploit the vulnerabilities within the dApp code logic or decentralized infrastructure to acquire unauthorized entry to non-public keys, person wallets, and delicate information.
Phishing assaults work by deceiving customers in order that they’ll reveal their non-public keys or any delicate data. Phishing is likely one of the confirmed and efficient approaches that hackers use to realize important data from customers. It is very important notice that hackers may use social engineering expertise for phishing assaults with out counting on technical data.
-
Good Contract Vulnerabilities
Web3 safety relies upon instantly on safety of sensible contracts as they’re the core parts of the web3 ecosystem. Any particular person who needs to study web3 safety finest practices should familiarize themselves with sensible contracts and the way they work. Good contracts work as automated agreements or transactions that might run independently upon satisfying sure circumstances. Flaws within the sensible contract may result in unimaginable outcomes, akin to unintended actions and lack of funds.
Excited to study concerning the important vulnerabilities and safety dangers in sensible contract growth, Enroll now within the Good Contracts Safety Course
Decentralized purposes, or dApps, are additionally a core factor of the web3 ecosystem and will result in completely different safety dangers. dApps function various kinds of vulnerabilities, together with backdoors and logic vulnerabilities that might open the doorways for hackers to take advantage of the contracts.
One other noticeable sort of assault in web3 refers to provide chain assaults wherein attackers exploit a selected element of the web3 software. For instance, attackers may exploit an open-source library carried out within the code of a web3 software.
Zero-day exploits additionally have an effect on safety in web3 by exposing a vulnerability throughout the web3 neighborhood. It capitalizes on the lack of knowledge a few particular vulnerability. Attackers may capitalize on such vulnerabilities to acquire unauthorized entry to methods, deploy malware, or steal information.
Web3 customers should additionally take note of privateness dangers akin to metadata leakage. Metadata refers back to the information that might expose vital details about person transactions, akin to sender and recipient addresses. You may marvel concerning the issues with metadata for web3 cybersecurity with the immutability of blockchain. It’s true that nobody can modify the transaction information on blockchain. Nevertheless, malicious brokers can use the metadata of a transaction to attract inferences about delicate data of customers.
The issues for web3 safety additionally emerge from the modern developments within the web3 ecosystem. Blockchain analytics makes use of information analytics methods for tracing the transaction circulate on blockchain. It could possibly serve promising outcomes for personalization of companies for web3 customers.
Alternatively, blockchain analytics may additionally expose delicate details about customers, together with the identification of the person and quantity of transactions. The probabilities of metadata leakage complement the dangers related to blockchain analytics by risking publicity to delicate information.
Greatest Practices for Safeguarding Your Property in Web3
The checklist of safety dangers in web3 is considerably in depth, and new sorts of safety dangers emerge day-after-day. On the identical time, the rising adoption of web3 additionally makes it a promising goal for attackers. Cryptocurrencies, NFTs, digital actual property, and plenty of different property are making their means into web3, which improves the worth of property locked within the web3 panorama. Listed below are a number of the finest practices it’s best to observe for securing your property in web3.
The most important threat in web3 is the specter of non-public key theft. Non-public keys aid you acquire management over your cryptocurrency and digital property in web3. The most effective strategy for securing digital property is to forestall anybody from accessing your non-public keys. Apparently, you possibly can depend on a {hardware} pockets for storing your cryptocurrencies and digital property with safety. {Hardware} wallets retailer your non-public keys in offline storage with bodily units. Widespread examples of {hardware} wallets embrace Trevor and Ledger. It’s also possible to make the most of the {hardware} wallets as an extra layer for Metamask.
-
Apply Warning with the Restoration Phrase
The restoration phrase or seed phrase is one other essential piece of knowledge that it’s best to safeguard in any respect prices. The seed phrase features a mixture of 12 to 24 phrases, which can assist in recovering your non-public keys. Yow will discover references to safeguards for the seed phrase in responses to “What’s web3 safety?” as one of many widespread recommendations for web3 safety. Do not forget that it’s best to by no means share your restoration phrase with anybody or retailer it on-line. You possibly can write down the restoration phrase on a bit of paper and retailer it in a safe location that solely you possibly can entry.
-
Make the most of Two-Issue Authentication
One other confirmed advice for safeguarding your digital property in web3 is two-factor authentication. You possibly can study web3 safety solely by following a number of the typical tenets in web2 cybersecurity. Two-factor authentication has served as an efficient layer of safety for web2 purposes, and it may work in the identical means for web3.
The second issue implies that you’d obtain a code in your cellphone or one generated by an authentication app. Two-factor authentication may assist in stopping unauthorized entry when somebody has compromised your password. Majority of web3 purposes present the ability of two-factor authentication, and customers ought to at all times allow it in all circumstances.
Curious to develop an in-depth understanding of web3 software structure? Enroll now within the Web3 Software Improvement Course
How Can You Select the Proper Instruments for Securing Your Digital Property?
Web3 customers should take accountability for securing digital property of their web3 expertise. Due to this fact, it is very important choose the precise instruments that might defend your digital property towards safety threats. You possibly can depend on efficient web3 safety software program to keep away from unwarranted compromises of your digital property. Listed below are a number of the options it’s best to search for in a device for securing web3 property.
Initially, it’s essential to select web3 safety software program with real-time safety. The software program should present real-time transaction audits to determine dangerous logic alongside important vulnerabilities. As well as, it should even have a extremely responsive notification or reporting mechanism for warning customers.
One other vital requirement for safety in web3 would level to anti-phishing options. Phishing is a significant safety threat in web3, and anti-phishing options assist in simpler detection of phishing web sites. It may assist in blocking malicious web sites and safeguarding your beneficial property.
Most vital of all, the web3 safety software program should obtain common updates to determine newest threats. Updates are an vital requirement for guaranteeing efficient safeguards towards rising threats to web3 safety.
Begin your journey to turning into an professional in Web3 safety expertise with the steerage of business specialists via Web3 Safety Skilled Profession Path
Conclusion
The most effective practices for safeguarding your digital property in web3 would give attention to stopping any vulnerabilities in sensible contract code. As well as, customers should additionally perceive the implications of various web3 safety dangers and their origins. Web3 is a quickly rising business with the introduction of modern options like NFTs, metaverse, and web3 video games. The excessive worth of property in web3 has turned web3 right into a looking floor for malicious actors.
On prime of it, the profitable propositions for fast income in web3 may deceive customers into giving up delicate data. Due to this fact, it is very important find out about web3 safety and the perfect practices for safeguarding your property. Familiarize your self with the fundamentals of web3 and determine how one can guarantee the perfect safety in your web3 property.
*Disclaimer: The article shouldn’t be taken as, and isn’t meant to offer any funding recommendation. Claims made on this article don’t represent funding recommendation and shouldn’t be taken as such. 101 Blockchains shall not be accountable for any loss sustained by any one that depends on this text. Do your personal analysis!






Thank you for the auspicious writeup It in fact was a amusement account it Look advanced to more added agreeable from you By the way how could we communicate