
Researchers have found a intelligent piece of malware that stealthily exfiltrates information and executes malicious code from Home windows programs by abusing a function in Microsoft Web Info Providers (IIS).
IIS is a general-purpose net server that runs on Home windows gadgets. As an online server, it accepts requests from distant purchasers and returns the suitable response. In July 2021, community intelligence firm Netcraft mentioned there have been 51.6 million situations of IIS unfold throughout 13.5 million distinctive domains.
IIS presents a function known as Failed Request Occasion Buffering that collects metrics and different information about net requests acquired from distant purchasers. Consumer IP addresses and port and HTTP headers with cookies are two examples of the info that may be collected. FREB helps directors troubleshoot failed net requests by retrieving ones assembly sure standards from a buffer and writing them to disk. The mechanism might help decide the reason for 401 or 404 errors or isolate the reason for stalled or aborted requests.
Legal hackers have found out the right way to abuse this FREB function to smuggle and execute malicious code into protected areas of an already compromised community. The hackers may use FREB to exfiltrate information from the identical protected areas. As a result of the method blends in with professional eeb requests, it supplies a stealthy solution to additional burrow into the compromised community.
The post-exploit malware that makes this attainable has been dubbed Frebniis by researchers from Symantec, who reported on its use on Thursday. Frebniis first ensures FREB is enabled after which hijacks its execution by injecting malicious code into the IIS course of reminiscence and inflicting it to run. As soon as the code is in place, Frebniis can examine all HTTP requests acquired by the IIS server.
“By hijacking and modifying IIS net server code, Frebniis is ready to intercept the common circulate of HTTP request dealing with and search for specifically formatted HTTP requests,” Symantec researchers wrote. “These requests permit distant code execution and proxying to inner programs in a stealthy method. No recordsdata or suspicious processes will probably be working on the system, making Frebniis a comparatively distinctive and uncommon kind of HTTP backdoor seen within the wild.”
Earlier than Frebniis can work, an attacker should first hack the Home windows system working the IIS server. Symantec researchers have but to find out how Frebniis does this.
Frebniis parses all HTTP POST requests invoking the logon.aspx or default.aspx recordsdata, that are used to create login pages and serve default net pages, respectively. Attackers can smuggle requests into an contaminated server by sending certainly one of these requests and including the password “7ux4398!” as a parameter. As soon as such a request is acquired, Frebniis decrypts and executes .Internet code that controls the principle backdoor capabilities. To make the method extra stealthy, the code drops no recordsdata to disk.
The .NET code serves two functions. First, it supplies a proxy that permits attackers to make use of the compromised IIS server to work together or talk with inner assets that may in any other case be inaccessible from the Web. The next desk exhibits the instructions it’s programmed to hold out:
| Command | Operate identify | Parameter | Description |
|---|---|---|---|
| 1 | CreateConnect | Host:Port | Connect with a distant system for proxying, returns a UUID representing the distant system |
| 2 | ReadScoket | Uuid | Learn a Base64 string from a distant system |
| 3 | Writescoket | Uuid, Base64 string | Write a Base64 string to a distant system |
| 4 | CloseScoket | Uuid | Shut the connection |
The second objective of the .Internet code is to permit the distant execution of attacker-provided code on the IIS server. By sending a request to the logon.aspx or default.aspx recordsdata that features code written in C#, Frebniis will robotically decode it and execute it in reminiscence. As soon as once more, by executing the code immediately in reminiscence, the backdoor is way tougher to detect.
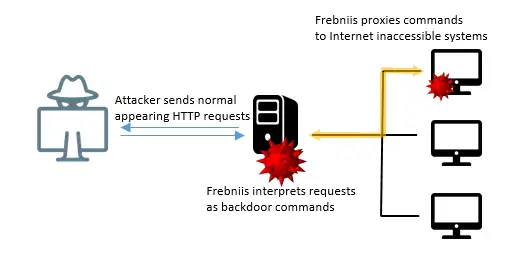
Diagram exhibiting how Frebniis is used.
Symantec
It’s not clear how broadly used Frebniis is in the meanwhile. The put up supplies two file hashes related to the backdoor however doesn’t clarify the right way to search a system to see in the event that they exist.

